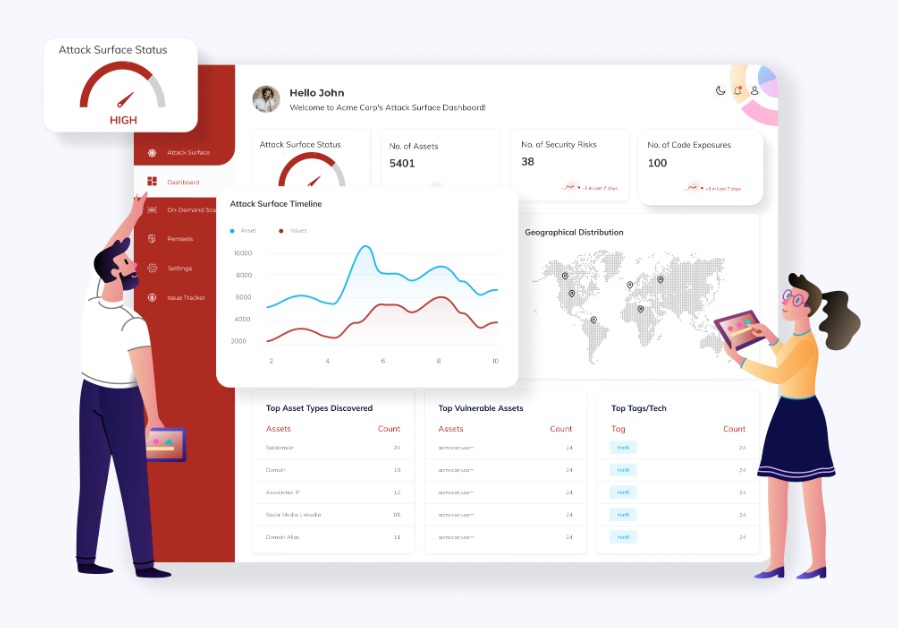
Discover your Attack
Surface Continuously
We profile your assets using multiple techniques and maintains a comprehensive inventory of your assets. This allows you to manage your external infrastructure and prioritize your actions. No false positives and filling noise
Get Help